How does one patch or prevent a BufferOverRun??
From the start - don't stuff more bytes into a buffer than it can hold.
More specifically (this applies to C/C++; a lot of these problems don't occur in other languages):
- If writing code in C++, use the string class rather than char[] for strings whenever performance isn't a priority.
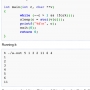
- Never use gets() -- always use fgets()
- Never use sprintf(), use snprintf() instead
- Never use strcpy(), use strncpy() instead
- Never use strcat(), use strncat() instead
- Never use printf (foo) to print a raw string; always use printf ("%s", foo). Especially important if foo is a string generated by a user. One class of attacks is to embed nasty formatting controls (like %n) in a string, trying to cause a buffer overflow. (See FormatStringVulnerability?)
- If you have to use char[] rather than string, keep track of your buffer lengths.
- Never assume a 4K or other size buffer is "long enough"... chances are it won't be.
- Use dynamic char buffers, and DoubleAfterFull to maintain good performance.
The best way to avoid buffer overruns and the related list overruns and list jams is to make a religion of testing your boundary conditions, testing your boundary assumptions and, most important, any programmer whose code allows them should be subjected to the most severe ridicule and humiliation the team's culture will allow. Dunce caps are easy to make and very effective.